B1-Motivation
B1 Motivation
IT systems, including IoT systems, can be compromised by cyber-attacks in their supply chain. Components compromised in the supply chain open the way for a variety of exploits when deployed into operational environments. Supply chain attacks are extremely cost effective from attackers’ points of view. IT assets coming from development, manufacturing and distribution environments are often trusted implicitly by downstream users, despite weak or unknown security controls in those environments. Furthermore, a successful compromise of a single well-chosen IT vendor environment can fan out to the vendor’s entire customer base as products and software updates are deployed. It is no coincidence that many of the most notorious cyber attacks have been supply chain attacks.
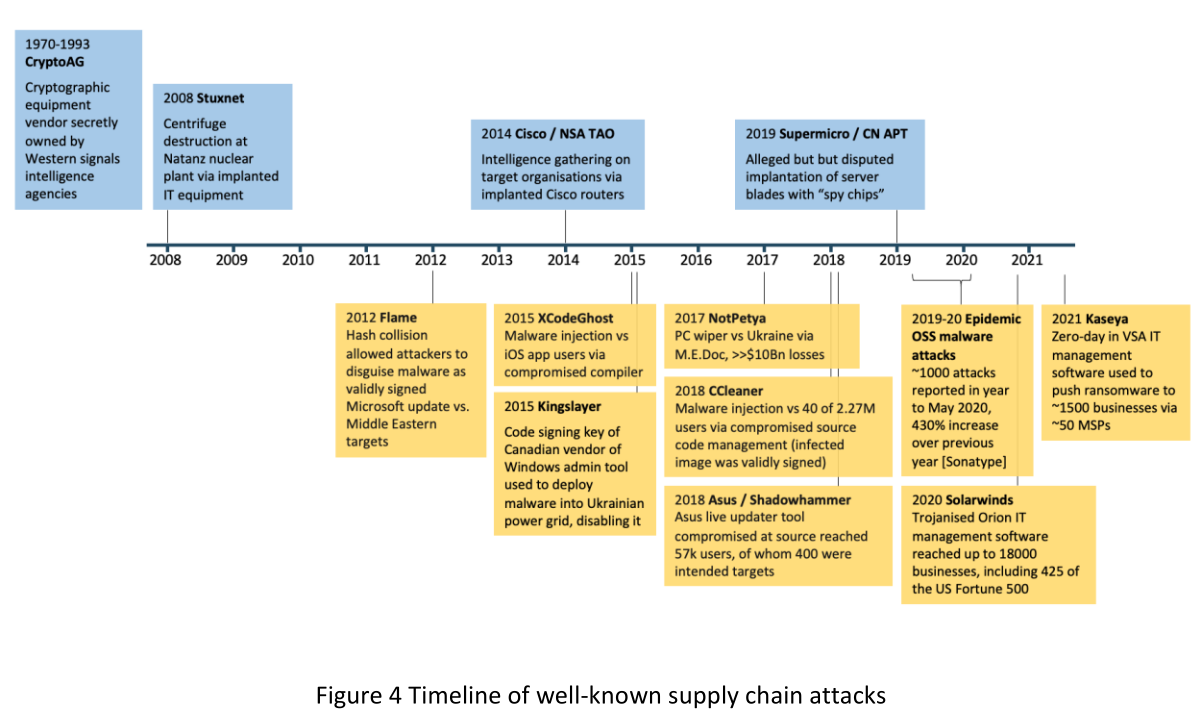
In recent years the ICT security literature has increasingly recognised the problem of protecting both software and hardware assets in the supply chain and has developed a variety of recommendations in response. However, while many of these recommendations are applicable to IoT devices, interpreting them requires a detailed understanding of the IoT supply chain. There is also a need for IoT-specific security recommendations to accommodate IoT device supply chains’ unique characteristics.
An IoTSF working group was formed in April 2020 to supply both these needs with an expanded and updated set of security requirements concerning smart devices’ supply chains. The group received contributions from 43 experts representing 34 organisations resulting in 29 specific, implementable recommendations. These have been mapped into this edition of the Framework in 5 pre-existing and 24 new requirements.