Risk-Assessment-Steps
1 Risk Assessment Steps
The core of the security process is to understand what is being protected and from what or whom. It is also
important to identify what is not being protected. There are many ways to accomplish this procedure, but it is
recommended to use well-known, best practice, risk management standards [ref 39, 40 and 41]123. Risk
management techniques can also be found in several common business training publications. An outline of the
Risk Assessment process used in this document can be seen in the flow diagram and bullet list below:
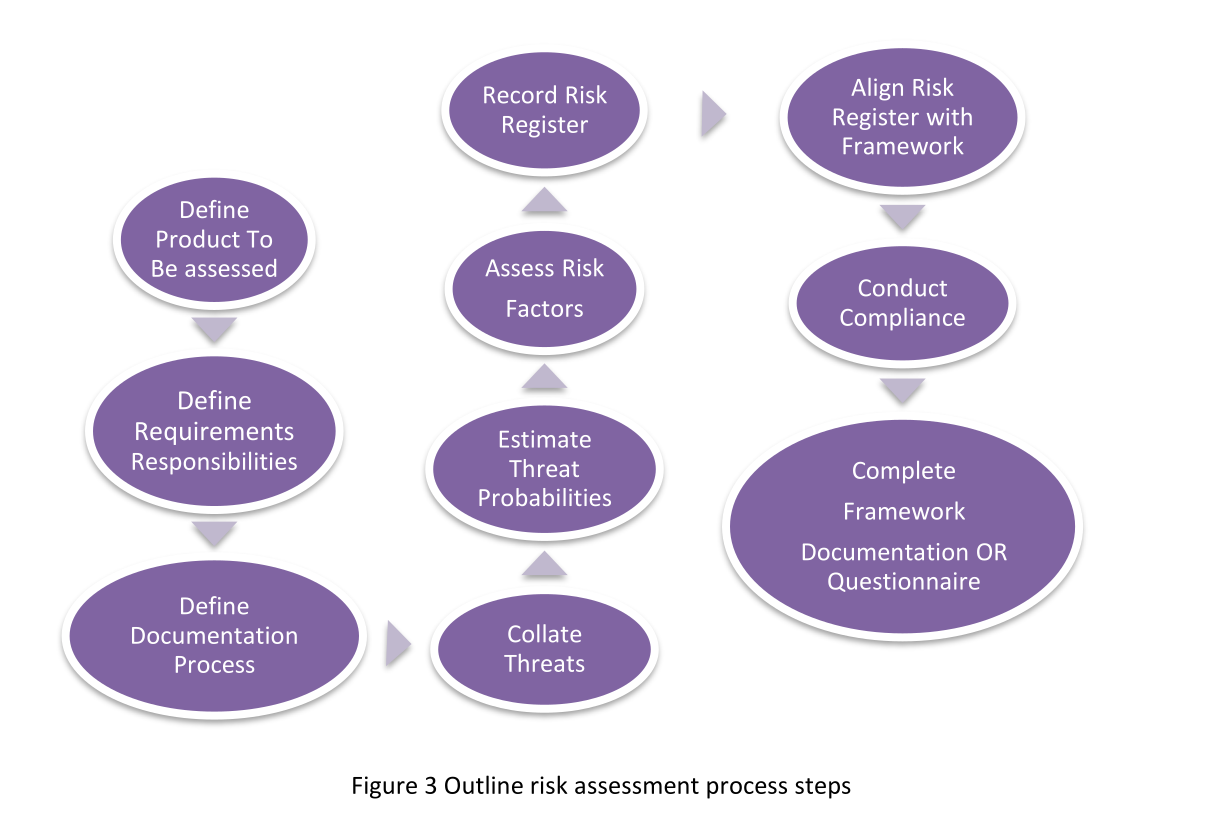
- Create a list of security risks to the product
- Use brainstorming techniques, mind mapping or other Group Creativity techniques.
- Generate a list covering both business and technical threats:
- E.g. “Brand Image damage due to adverse publicity”, “cost of product recall”, “product exposes users Wi-Fi credentials”
- Safety aspects of the product that affect users if the security is compromised
- The Framework can be used to support the creation of the list of risks by considering the Assurance Class criteria
- Assess the “probability” of each item on the Risk List happening
- Assess the “Cost” (impact in terms of the detectability and recovery) of each item on the Risk List – if it happens
- Multiply the Cost by the Probability, this gives a “Risk Factor”
- Order list by “Risk Factor”. This could be a percentage or simply Probability x Impact number
This list becomes the “Risk Register” document and may then be used to guide and justify the work needed to address product security. The aim of the work is to reduce the risk “probability” factor to an acceptable level.
| Threat Description | Probability (0-100%) | Impact/Cost to company of threat happening (0-5) | Risk Factor |
|---|---|---|---|
| Compromise of Encryption and Key Management | 5% | 5 | (0.05*5) = 0.25 |
| Web User Interface subversion | 90% | 4 | (0.9*4) =3.6 |
| Mobile Application hacked | 15% | 2 | (0.15*2) = 0.3 |
| Leakage of Private personal data | 15% | 5 | (0.15*5) = 0.75 |
Table 5
This is showing the biggest risk is the web User Interface, so the priority should be on mitigating this to reduce the probability.
Footnotes
-
Bluetooth Numeric Comparison [ https://csrc.nist.gov/publications/detail/sp/800-121/rev-1/archive/2012-06-11 ] ↩
-
UK Government Cyber security risk assessment guidance [https://www.ncsc.gov.uk/guidance/risk-management-collection] ↩
-
NIST Special Publication 800-30 guidance for conducting risk assessments [ https://www.nist.gov/publications/guide-conducting-risk-assessments] ↩